Table of Contents
- How HTTP Cookies Work
- Essential Cookie Security Attributes
- CORS and Cross-Origin Cookie Management
- Practical Implementation Examples
- Cookie Troubleshooting Guide
- Frequently Asked Questions
HTTP cookies are fundamental building blocks of modern web development, enabling session management, user authentication, and personalized experiences across websites. Despite their widespread use, many developers struggle with cookie security attributes, cross-origin request handling, and proper CORS implementation.
This comprehensive guide covers everything you need to know about HTTP cookies, from basic concepts to advanced security configurations. You'll learn how to implement secure cookies using attributes like HttpOnly, Secure, and SameSite, while mastering cross-origin resource sharing (CORS) for modern web applications.
How HTTP Cookies Work
HTTP cookies are small data files stored in web browsers, created when servers send a Set-Cookie header in HTTP responses. Once stored, browsers automatically include these cookies in subsequent requests to the same domain, making them perfect for session management and user state tracking.
The Cookie Lifecycle Process
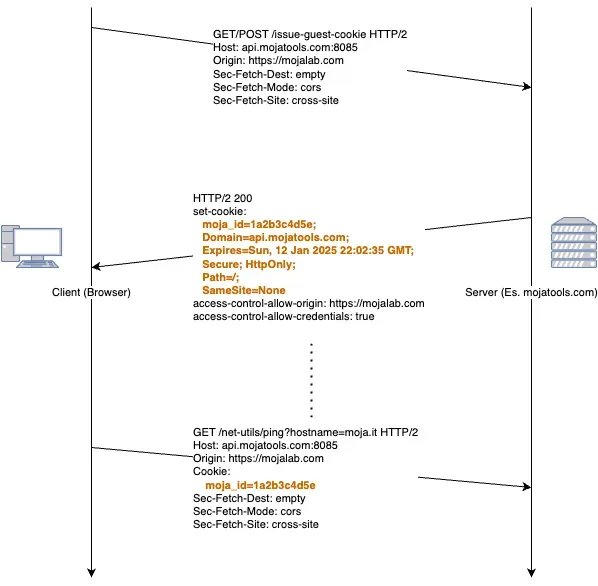
When a user visits your website, here's exactly what happens:
- Server Response: Your backend sends a
Set-Cookieheader containing the cookie data - Browser Storage: The user's browser stores the cookie locally
- Automatic Inclusion: On future requests, browsers automatically send stored cookies
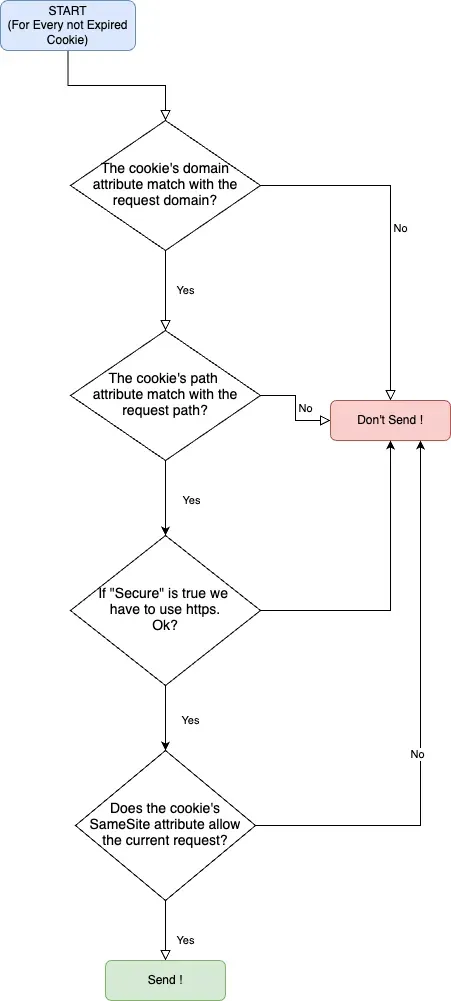
- Conditional Sending: Cookies are only sent when specific conditions are met (domain, path, security attributes)
The browser follows a strict decision tree when determining whether to send cookies:
Did you know? Netscape Navigator introduced HTTP cookies in 1994, followed by Internet Explorer in 1995. These early innovations shaped how we handle user sessions across the modern web.
Essential Cookie Security Attributes
Understanding cookie security attributes is crucial for protecting your web applications from common attacks like Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF).
Complete Cookie Attributes Reference
| Attribute | Security Purpose | Example Usage |
|---|---|---|
| Name-Value | Core cookie data | session_id=abc123 |
| HttpOnly | Prevents XSS attacks | HttpOnly=True |
| Secure | HTTPS-only transmission | Secure=True |
| Domain | Scope control | Domain=api.mojatools.com |
| Path | URL path restriction | Path=/ |
| SameSite | CSRF protection | SameSite=None |
HttpOnly Attribute for XSS Prevention
The HttpOnly attribute prevents JavaScript from accessing cookies through document.cookie, making it impossible for malicious scripts to steal session cookies during XSS attacks.
Security Benefits:
- Blocks client-side cookie access via JavaScript
- Prevents session hijacking through XSS vulnerabilities
- Essential for authentication and session cookies
- Should be combined with Secure flag for maximum protection
SameSite Attribute for CSRF Protection
The SameSite attribute controls when browsers send cookies in cross-origin requests, providing powerful CSRF attack prevention.
SameSite=Strict (Maximum Security)
Cookie Behavior: Never sent in cross-origin requests
Use Case: Highly sensitive operations
Example: Banking applications, admin panels
Security Level: Highest
Real-world scenario: User visits malicious-site.com which tries to make a request to your banking application at secure-bank.com. With SameSite=Strict, the authentication cookie won't be sent, blocking the attack.
SameSite=Lax (Balanced Approach)
Cookie Behavior: Sent for top-level navigation, blocked for cross-origin AJAX
Use Case: Standard web applications
Example: E-commerce sites, content platforms
Security Level: Moderate
Practical example: User clicks a link from google.com to visit your site - cookies are sent. However, if evil-site.com makes an AJAX request to your API, cookies are blocked.
SameSite=None (Cross-Origin Required)
Cookie Behavior: Always sent (requires Secure=true)
Use Case: Third-party integrations, SSO systems
Example: Payment gateways, social login
Security Level: Requires additional protections
Important: SameSite=None requires HTTPS and the Secure attribute to function properly.
Setting Secure Cookies with Python Flask
Here's how to implement secure cookie configuration using Flask web framework:
from flask import make_response, jsonify
def set_secure_cookie():
"""Set a secure session cookie with all security attributes"""
resp = make_response(jsonify({"message": "Secure cookie set successfully"}))
resp.set_cookie(
"session_id", # Cookie name
"secure_session_value_123", # Cookie value
httponly=True, # Prevent XSS attacks
secure=True, # HTTPS only
samesite="None", # Allow cross-origin
path="/", # Site-wide access
domain="api.mojatools.com", # Restrict to API domain
max_age=3600 # 1 hour expiration
)
return resp
Cookie Security Configuration Explained
| Setting | Security Purpose | Impact |
|---|---|---|
httponly=True |
XSS protection - blocks JavaScript access | Prevents session hijacking |
secure=True |
HTTPS enforcement - encrypted transmission only | Protects against man-in-the-middle attacks |
samesite="None" |
Cross-origin enabled - allows third-party requests | Enables modern SPA architectures |
path="/" |
Site-wide scope - accessible across all URLs | Simplifies session management |
domain="..." |
Domain restriction - limits cookie scope | Prevents subdomain attacks |
JavaScript Fetch API with Cookies
When building single-page applications (SPAs) with separate frontend and backend domains, proper cookie handling in JavaScript is essential.
Cross-Origin Cookie Implementation
// Making authenticated API calls with automatic cookie inclusion
async function fetchWithCookies() {
try {
const response = await fetch("https://api.mojatools.com/user/profile", {
method: "GET",
credentials: "include", // Critical: includes cookies in cross-origin requests
headers: {
"Content-Type": "application/json"
}
});
if (!response.ok) {
throw new Error(`HTTP ${response.status}: ${response.statusText}`);
}
const userData = await response.json();
console.log("User profile loaded:", userData);
return userData;
} catch (error) {
console.error("Authentication failed:", error);
// Handle authentication errors (redirect to login, show error message, etc.)
throw error;
}
}
Key Implementation Details:
credentials: "include"is mandatory for cross-origin cookie transmission- Server must return proper CORS headers including
Access-Control-Allow-Credentials: true - Cookies must meet SameSite, Secure, and Domain requirements
- Always implement error handling for authentication failures
CORS and Cross-Origin Cookie Management
Cross-Origin Resource Sharing (CORS) enables secure cross-domain API access while maintaining proper cookie handling for authentication and session management.
Understanding the CORS Preflight Process
Modern browsers implement a sophisticated CORS preflight mechanism for complex cross-origin requests:
1. Browser Initiates Preflight Check
OPTIONS /api/user-data HTTP/1.1
Host: api.mojatools.com
Origin: https://mojalab.com
Access-Control-Request-Method: POST
Access-Control-Request-Headers: content-type, authorization
2. Server Responds with CORS Policy
HTTP/1.1 200 OK
Access-Control-Allow-Origin: https://mojalab.com
Access-Control-Allow-Credentials: true
Access-Control-Allow-Headers: content-type, authorization
Access-Control-Allow-Methods: GET, POST, PUT, DELETE, OPTIONS
Access-Control-Max-Age: 86400
3. Browser Evaluates Permission
The browser checks if the server's CORS policy matches the request requirements. If approved, the actual request proceeds with automatic cookie inclusion.
4. Actual Request with Cookies
POST /api/user-data HTTP/1.1
Host: api.mojatools.com
Origin: https://mojalab.com
Cookie: session_id=abc123; auth_token=xyz789
Content-Type: application/json
Flask CORS Configuration for Cookies
from flask_cors import CORS
from flask import Flask
app = Flask(__name__)
# Configure CORS to allow credentials (cookies) from specific origin
CORS(app,
resources={
r"/api/*": {
"origins": ["https://mojalab.com"], # Specific domain only
"supports_credentials": True, # Allow cookies
"allow_headers": ["Content-Type", "Authorization"],
"methods": ["GET", "POST", "PUT", "DELETE", "OPTIONS"]
}
})
Security Best Practices:
- Never use
origins: ["*"]withsupports_credentials: True - Specify exact domains rather than wildcards
- Limit allowed methods to what your API actually supports
- Set appropriate cache duration with
Access-Control-Max-Age
Cookie Troubleshooting Guide
When cross-origin cookies aren't working, follow this systematic troubleshooting approach:
Step-by-Step Debugging Process
| Issue Category | Diagnostic Steps | Common Solutions |
|---|---|---|
| Browser DevTools | Check Application → Cookies tab | Verify cookie is actually set with correct attributes |
| Network Tab | Inspect request/response headers | Confirm Set-Cookie and CORS headers are present |
| HTTPS Requirements | Verify Secure cookies use HTTPS |
Switch to HTTPS or remove Secure attribute in development |
| SameSite Configuration | Test different SameSite values | Use SameSite=None for cross-origin, ensure Secure=True |
| CORS Headers | Validate server CORS configuration | Set Access-Control-Allow-Credentials: true |
| Browser Extensions | Disable ad blockers temporarily | Some extensions block third-party cookies |
| Domain Matching | Check cookie domain vs. request URL | Ensure cookie domain matches or is parent of request domain |
Common Cookie Problems and Solutions
Problem: Cookies not sent in cross-origin requests
// ❌ Wrong - missing credentials
fetch("https://api.example.com/data")
// ✅ Correct - includes cookies
fetch("https://api.example.com/data", {
credentials: "include"
})
Problem: SameSite=None without Secure
# ❌ Wrong - SameSite=None requires Secure
resp.set_cookie("session", "value", samesite="None")
# ✅ Correct - both attributes together
resp.set_cookie("session", "value", samesite="None", secure=True)
Problem: Incorrect CORS configuration
# ❌ Wrong - wildcard with credentials
CORS(app, origins=["*"], supports_credentials=True)
# ✅ Correct - specific origin with credentials
CORS(app, origins=["https://myapp.com"], supports_credentials=True)
Frequently Asked Questions
What are HTTP cookies used for?
HTTP cookies serve multiple purposes in web development:
- Session management: Maintaining user login state across page loads
- Personalization: Storing user preferences and settings
- Tracking: Analytics and user behavior analysis
- Shopping carts: Preserving e-commerce cart contents
- Authentication: Storing secure tokens for API access
Are cookies secure by default?
No, cookies require explicit security configuration. Without proper attributes:
- JavaScript can access cookie data (XSS vulnerability)
- Cookies transmit over unencrypted HTTP connections
- Cross-site request forgery (CSRF) attacks are possible
- Malicious websites can potentially access cookies
Always implement HttpOnly, Secure, and SameSite attributes for sensitive cookies.
How do I delete cookies properly?
To delete cookies from both client and server side:
JavaScript (client-side):
document.cookie = "session_id=; expires=Thu, 01 Jan 1970 00:00:00 UTC; path=/;";
Flask (server-side):
resp.set_cookie("session_id", "", expires=0)
Can cookies work without JavaScript enabled?
Yes! HTTP cookies work at the browser level and don't require JavaScript. They're automatically sent with HTTP requests regardless of JavaScript availability, making them reliable for server-side session management.
What's the difference between cookies and localStorage?
| Feature | Cookies | localStorage |
|---|---|---|
| Automatic sending | Yes - included in HTTP requests | No - JavaScript only |
| Storage size | ~4KB per cookie | ~5-10MB total |
| Expiration | Server-controlled | Persistent until cleared |
| Security | HttpOnly option available | Always accessible via JS |
| Cross-origin | Controlled by SameSite | Same-origin only |
Advanced Cookie Security Best Practices
Production Security Checklist
- ✅ Always use
HttpOnlyfor session cookies - ✅ Implement
Secureattribute in production (HTTPS) - ✅ Configure appropriate
SameSitepolicy - ✅ Set reasonable expiration times (
Max-Age) - ✅ Use specific
DomainandPathrestrictions - ✅ Implement proper CORS configuration
- ✅ Regular security audits and penetration testing
- ✅ Monitor for suspicious cookie-related activities
Cookie Performance Optimization
Minimize cookie size: Each cookie adds overhead to every HTTP request
Use efficient serialization: JSON is often more compact than other formats
Implement cookie compression: For large data payloads
Cache cookie validation: Reduce database lookups for session verification
💡 Quick Reference Links
| Resource Type | Best For | Link |
|---|---|---|
| Official Spec | Implementation reference | RFC 6265 |
| Developer Guide | Practical examples | MDN Cookies |
| Security Best Practices | Security hardening | OWASP Cookie Guide |
| CORS Implementation | Cross-origin setup | W3C CORS Spec |
| Testing Tools | Development debugging | Chrome DevTools |
Last updated: August 2025 | All links verified and active
Conclusion
HTTP cookies remain essential for modern web development, providing robust session management and user authentication capabilities. By implementing proper security attributes (HttpOnly, Secure, SameSite) and correctly configuring CORS policies, you can build secure, scalable web applications that protect user data while maintaining excellent user experience.
Key takeaways for successful cookie implementation:
- Always prioritize security with proper attribute configuration
- Understand cross-origin implications for modern SPA architectures
- Implement comprehensive error handling and fallback mechanisms
- Regular testing and monitoring of cookie behavior across different browsers
- Stay updated with evolving browser policies and security standards
Disclaimer: At MojaLab, we aim to provide accurate and useful content, but hey, we’re human (well, mostly)! If you spot an error, have questions, or think something could be improved, feel free to reach out—we’d love to hear from you. Use the tutorials and tips here with care, and always test in a safe environment. Happy learning!

